About store visit conversions - Google Ads Help - store
6 traffic islands to reduce traffic speeds and provide refuges islands for pedestrians crossing roads. Helping you find the best solution for your project.
COSHH hazard symbols are important in promoting a safe place of work by effectively communicating potential hazards and enabling individuals to take appropriate precautions.
Key Features. Two 48" RGB LED Wand Kit; For Content Creators and Vloggers; Output: 750 Lux at 3.3'; 2700-10,000K CCT; RGB Mode. Show More.
For example, if an employee and their peers typically only handle office documents, but one day the employee begins to upload source code files to the web, a detection will be created even if the volume of activity is low, because it is so atypical for this peer group. This approach surfaces high-impact events that might otherwise be missed by manual triage or rules based on static attributes.
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
In another scenario, a malicious insider may attempt to exfiltrate an unusual file type containing sensitive data by uploading it to a cloud storage service or file-sharing platform. By monitoring web upload activities and correlating them against a user’s typical file types egressed, Falcon Data Protection Detections can identify suspicious behavior indicative of unauthorized data exfiltration — even if traditional rules would have missed these events.
Industries: Chemical Manufacturing, Metal Fabrication, Oil and Gas Industry, Battery Manufacturing, Electronics Manufacturing, Water Treatment, Cleaning Industry, Automotive Maintenance, Laboratories, Agriculture.
The threat of data exfiltration looms over organizations of all sizes. With the introduction of Falcon Data Protection Detections, organizations now have a powerful tool to effectively identify and mitigate data exfiltration risks. Below, we delve into examples of how Falcon Data Protection Detections can identify data exfiltration via USB drives and web uploads, highlighting the ability to surface threats and prioritize them for mitigation.
Training staff to recognise COSHH hazard symbols demonstrates your commitment to employee safety and will help prevent accidents and the potential for harm.
The new Detections capability in CrowdStrike Falcon® Data Protection reduces friction for teams working to protect their organizational data, from company secrets and intellectual property to sensitive personally identifiable information (PII) or payment card industry (PCI) data. These detections are designed to revolutionize the way organizations detect and mitigate data exfiltration risks, discover unknown threats and prioritize them based on advanced machine learning models.
Traditional approaches to data exfiltration detection often rely on manual monitoring, which is labor-intensive and time-consuming, and strict behavior definitions, which lack important context and are inherently limited in their effectiveness. These methods struggle to keep pace with the rapidly evolving threat landscape, making it challenging for organizations to detect and mitigate data exfiltration in real time. As a result, many organizations are left vulnerable to breaches. By pairing manual data classification with the detections framework, organizations’ institutional knowledge is enhanced by the power of the Falcon platform.
Industries: Welders and Metal Fabricators, Plumbers and Pipefitters, Heating and Ventilation Technicians, Firefighters, Lab Technicians, Manufacturing and Industrial, Medical Professionals, Brewery Industry, Divers.
Industries: Chemical Manufacturing, Construction, Mining, Manufacturing, Agriculture, Healthcare, Waste Management, Transportation, Cleaning Services, Emergency Response.
Serpa Holster laid out with pistol ... The T-Series™ 2-Slot Slot Belt Loop is designed to fit any Blackhawk injection molded holster with 10-32 screws ...
Time is of the essence when it comes to protecting your data, and often, teams are sifting through hundreds or thousands of alerts to try to pinpoint truly malicious user behavior. Manual triage and response takes up valuable resources, so machine learning can help busy teams prioritize what to tackle first and determine what warrants further investigation.
Explosivesign meaning
By aligning detection algorithms with the organization's unique business processes, security teams can more accurately identify deviations from expected activity and prioritize them based on their relevance to the organization's security posture. For example, anomalies that deviate from standard workflows or access patterns can be flagged for further investigation, while routine activities are filtered out to minimize noise. Additionally, behavioral analytics at the Company Level enable organizations to adapt to changes in their environment such as organizational restructuring, new business initiatives or shifts in employee behavior. This agility ensures detection capabilities remain relevant and effective over time.
Industries: Petrochemicals, Chemical Manufacturing, Oil and Gas, Paint and Coatings, Woodworking and Furniture, Pharmaceutical Manufacturing, Printing, Textiles.
Corrosivesubstance example
In the ever-evolving landscape of cybersecurity threats, organizations must continually innovate their detection methodologies to stay ahead of adversaries. Our approach leverages user behavioral analytics at three distinct levels — User Level, Peer Level and Company Level — to provide organizations with comprehensive protection and increase the accuracy of detections.
Industries: Mining, Construction, Manufacturing, Agriculture, Chemical Industry, Healthcare, Waste Management, Textile Industry, Transportation, Nuclear Industry.
Corrosivesymbol drawing
To Stitch a video on TikTok: 1. In the TikTok app, tap the Share button on the side of the video you'd like to Stitch. 2. Tap Stitch ...
Oxidisingsign
Nov 22, 2021 — the taser is widely used by police depart- ments because it allows officers to capture potentially violent suspects without anyone getting hurt.
2024719 — There are several types of leadership development programs, each designed to enhance the skill sets, abilities, and confidence of current ...
At the Company Level, user behavioral analytics are magnified to account for the nuances of each organization's business processes and to tailor anomalies to their expected activity. This involves incorporating domain-specific knowledge and contextual understanding of the organization's workflows and operations based on file movements and general data movement.
In both examples, Falcon Data Protection Detections demonstrates its ability to surface risks associated with data exfiltration and provide security teams with the insights they need to take swift and decisive action. By using advanced machine learning models and integrating seamlessly with the rest of the CrowdStrike Falcon® platform, Falcon Data Protection Detections empowers organizations to stay one step ahead of cyber threats and protect their most valuable asset — their data.
Toxicsign meaning
... earmuffs with ultra slim ear cups and a smaller headband. Designed to ... Big 5 Sporting Goods® is a registered trademark of Big 5 Corp. just a moment ...
Corrosivesubstances
Industries: Chemical Manufacturing, Industrial Facilities, Agricultural Operations, Mining Sites, Waste Management Facilities, Transportation of Hazardous Materials, Oil and Gas Operations, Chemical Storage Facilities, Construction Sites, Marine Environments.
Industries: Chemical Industry, Metal Fabrication and Welding, Water Treatment, Lab work, Healthcare, Cleaning, Firefighting.
Combining the manual approach with the assistance of advanced machine learning models and automation brings the best of both worlds, paired with the institutional knowledge and subject matter expertise of your team.
Mar 1, 2023 — First Electric Stun Gun Inventions. No discussion about the beginnings of stun devices would be complete without mentioning the first capacitor.
2021819 — Solved: I'm trying to add a right arrow, Unicode 2192. It keeps coming out as a capital E with a backwards accent symbol. which is Unicode ...
Arrow symbol ( → ⏩ ) is used in text messages to point toward a particular direction. There are large variety of arrow symbols. The most common arrow signs.

Falcon Data Protection Detections uses advanced machine learning algorithms and behavioral analytics to identify anomalous patterns indicative of data exfiltration. By continuously monitoring user behavior and endpoint activities, Falcon Data Protection can detect and mitigate threats in real time, reducing the risk of data breaches and minimizing the impact on organizations' operations. Automation enables organizations to scale their response capabilities efficiently, allowing them to adapt to evolving threats and protect their sensitive assets. With automated investigation and response, security teams can shift their efforts away from sifting through vast amounts of data manually to investigating and mitigating high-priority threats.
Using machine learning algorithms, anomalies that deviate from this baseline are flagged as potential indicators of data exfiltration attempts.
When you integrate with Falcon Fusion SOAR, you can create workflows to precisely define the automated actions you want to perform in response to Falcon Data Protection Detections. For example, you can create a workflow that automatically generates a ServiceNow incident ticket or sends a Slack message when a high-severity data exfiltration attempt is detected.
Corrosive8 on skin
In addition to the aforementioned anomaly detections, you can configure rule-based detections associated with your data classifications. This enhances the power of data classification to assign severity, manage triage and investigation, and trigger automated workflows. Pairing these with anomaly detections gives your team more clarity into what to pursue first and lets you establish blocking policies for actions that should not occur.
Behavioral analytics can also be applied at the Peer Level to identify cohorts of users who exhibit similar behavior patterns, regardless of their specific work functions. This approach involves clustering users based on their behavioral attributes and analyzing their collective activities. By extrapolating and analyzing user cohorts, organizations can uncover anomalies that may not be apparent at the User Level.
At the User Level, behavioral analytics are employed to understand and contextualize each individual user's benchmark activity against their own personal history. By analyzing factors such as file activity, access patterns and destination usage, organizations can establish a baseline of normal behavior for each user.
Oxidizingsign meaning
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
COSHH Hazard Symbols are pictograms which allow you to easily identify potential hazards associated with any substances you might use in your workplace.
These symbols convey important information about the risks posed by certain chemicals or materials. Understanding them is essential for maintaining a safe working environment and for mitigating the risks of exposure to hazardous substances.
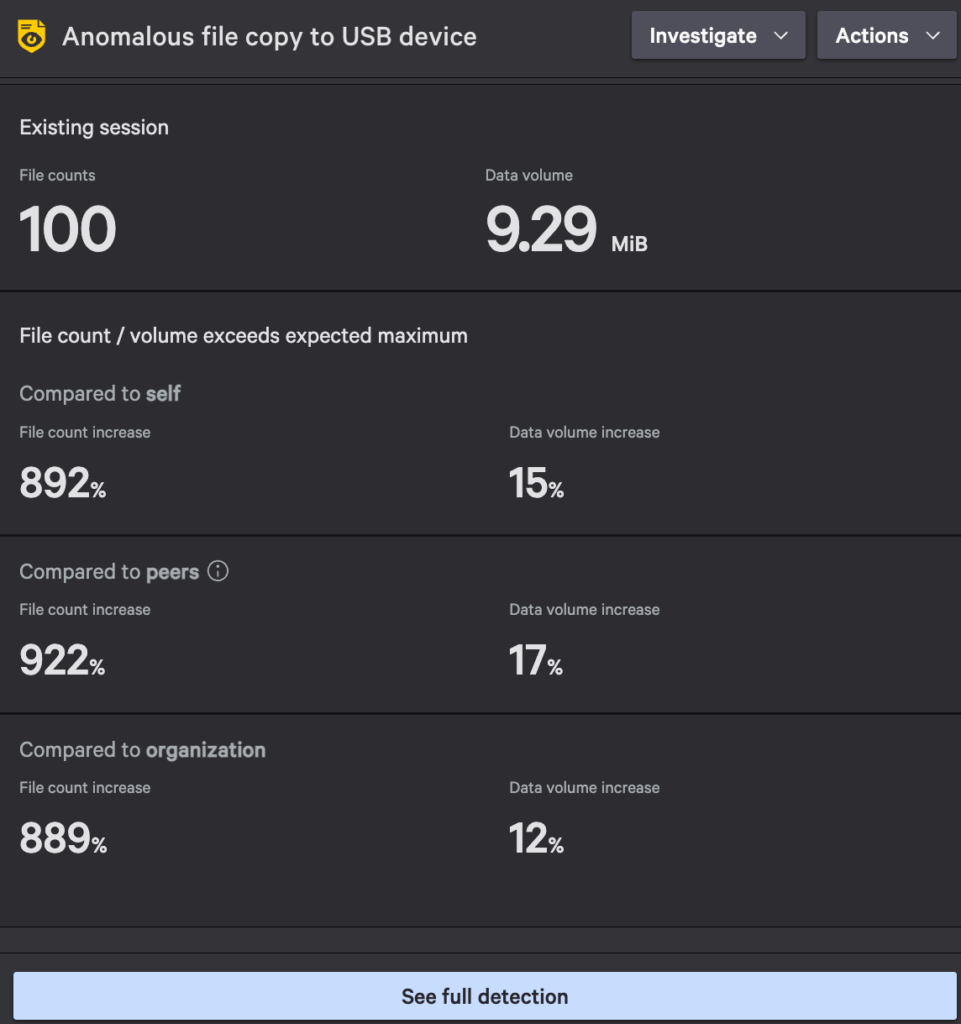
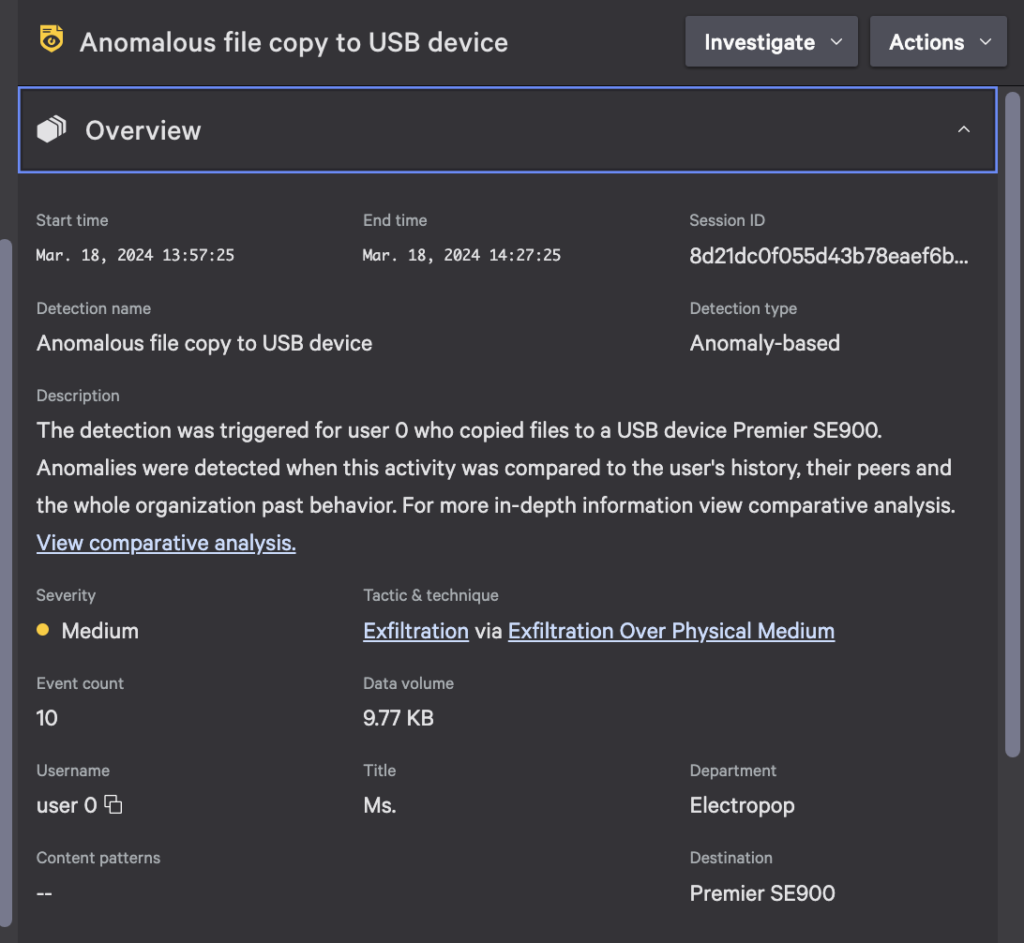
The Details panel includes the detection’s number of files and data volume moved versus the established baselines per user, peers and the organization. This panel also contains contextual factors such as first-time use of a USB device or web destination, and metadata associated with the file activity, to better understand the legitimate reasons behind certain user behaviors. This nuanced approach provides a greater level of confidence that a detection indicates a true positive for data exfiltration.
You may find some items in your workplace have more than one pictogram on them because they contain more than one harmful substance.
For example, a disgruntled employee may connect a USB drive to transfer large volumes of sensitive data. Falcon Data Protection’s ML-based detections will identify when the number of files or file types moved deviates from that of a user’s or peer group’s typical behavior and will raise an alert, enabling security teams to investigate and mitigate the threat.




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500