Paramotor helmet &Paragliding helmet more than 16 years ... - sky-hero
Effective CCTV signage not only helps you meet legal obligations but also demonstrates your commitment to creating a safe and secure environment for all who enter your premises. It fosters a sense of trust and accountability, showing that you prioritise the protection of individuals' rights and well-being.
Video and AudioSurveillanceSigns
In addition to the aforementioned anomaly detections, you can configure rule-based detections associated with your data classifications. This enhances the power of data classification to assign severity, manage triage and investigation, and trigger automated workflows. Pairing these with anomaly detections gives your team more clarity into what to pursue first and lets you establish blocking policies for actions that should not occur.
Videosurveillance signrequirements
Secure Redact. Somerset House, The Strand, London, WC2R 1LA Copyright 2024 Secure Redact. All rights reserved.
Consider the size and design of your CCTV signage as well; signs should be large enough to be easily noticed and read from a reasonable distance. Using high-contrast colours and clear, legible fonts can also enhance visibility.
It's worth noting that in addition to signage requirements, there are other important considerations when operating CCTV systems, such as why it’s important to blur faces on CCTV. Blurring or redacting identifying features can help protect individual privacy and ensure compliance with data protection regulations.
At the Company Level, user behavioral analytics are magnified to account for the nuances of each organization's business processes and to tailor anomalies to their expected activity. This involves incorporating domain-specific knowledge and contextual understanding of the organization's workflows and operations based on file movements and general data movement.
At the User Level, behavioral analytics are employed to understand and contextualize each individual user's benchmark activity against their own personal history. By analyzing factors such as file activity, access patterns and destination usage, organizations can establish a baseline of normal behavior for each user.
In the Great Teaching Toolkit Evidence Review we review the best bets for teachers to invest time and effort in if they want their students to learn more.
Signs must also be prominently displayed and easily visible to individuals entering the monitored area. They should additionally be placed at eye level and in well-lit locations to ensure readability - if your property has multiple entrances or extensive coverage, you may need to install multiple signs to ensure adequate notification.
CCTV signage serves several important purposes: first and foremost, it notifies individuals that they are entering an area monitored by security cameras. This transparency is crucial for maintaining trust and protecting privacy rights. Additionally, clear and visible signage can act as a deterrent against criminal activity, as potential offenders are aware that their actions may be recorded.
For example, if an employee and their peers typically only handle office documents, but one day the employee begins to upload source code files to the web, a detection will be created even if the volume of activity is low, because it is so atypical for this peer group. This approach surfaces high-impact events that might otherwise be missed by manual triage or rules based on static attributes.
Using machine learning algorithms, anomalies that deviate from this baseline are flagged as potential indicators of data exfiltration attempts.
Securitycamera signprintable
Conduct periodic walkthroughs of your property to verify that signs remain in good condition and have not been obscured or damaged. Replace or repair signage as needed to maintain clear communication with individuals entering the monitored areas.
By aligning detection algorithms with the organization's unique business processes, security teams can more accurately identify deviations from expected activity and prioritize them based on their relevance to the organization's security posture. For example, anomalies that deviate from standard workflows or access patterns can be flagged for further investigation, while routine activities are filtered out to minimize noise. Additionally, behavioral analytics at the Company Level enable organizations to adapt to changes in their environment such as organizational restructuring, new business initiatives or shifts in employee behavior. This agility ensures detection capabilities remain relevant and effective over time.
When installing CCTV cameras on your property, it's essential to comply with the signage requirements set forth by federal and state regulations. Proper signage not only informs individuals that they are being monitored but also helps protect your business from potential legal issues.
To maintain compliance, regularly assess your property to ensure that CCTV signage is present and visible in all areas monitored by security cameras. Pay special attention to entry points, high-traffic areas, and locations where individuals may have a heightened expectation of privacy, such as restrooms or changing rooms.
VideoSurveillanceSigns Amazon
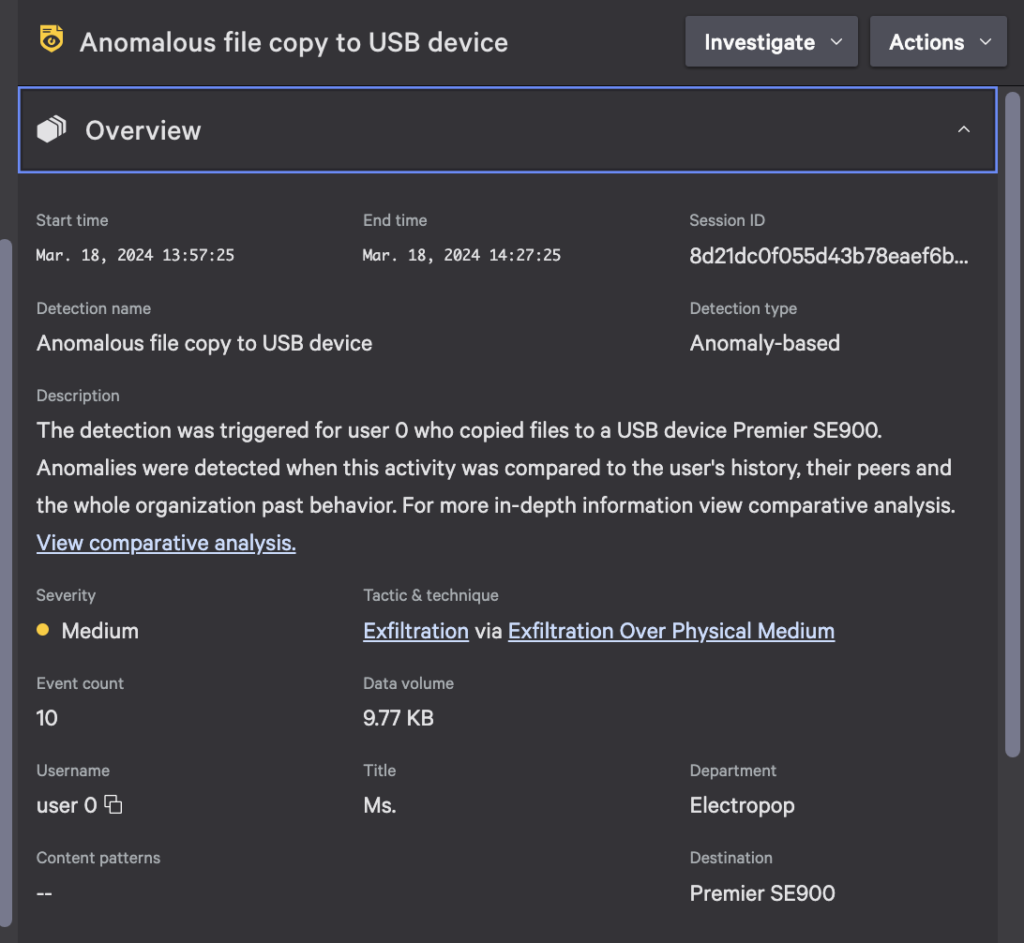
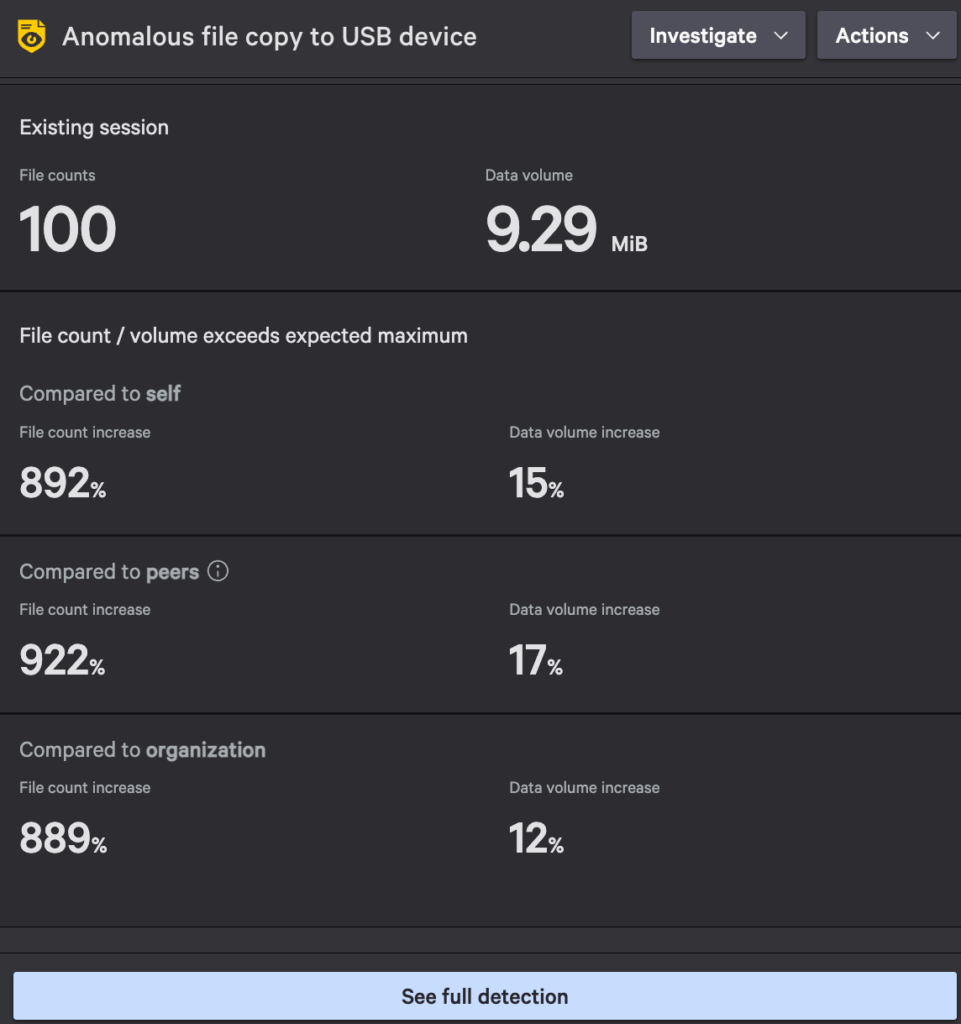
The Details panel includes the detection’s number of files and data volume moved versus the established baselines per user, peers and the organization. This panel also contains contextual factors such as first-time use of a USB device or web destination, and metadata associated with the file activity, to better understand the legitimate reasons behind certain user behaviors. This nuanced approach provides a greater level of confidence that a detection indicates a true positive for data exfiltration.
While there are no specific federal laws mandating CCTV signage, the use of security cameras is subject to various privacy and data protection regulations. The Fourth Amendment of the U.S. Constitution protects individuals against unreasonable searches and seizures, which extends to the use of surveillance technology. Furthermore, the Electronic Communications Privacy Act (ECPA) and the Stored Communications Act (SCA) regulate the interception and disclosure of electronic communications, including video recordings.
Time is of the essence when it comes to protecting your data, and often, teams are sifting through hundreds or thousands of alerts to try to pinpoint truly malicious user behavior. Manual triage and response takes up valuable resources, so machine learning can help busy teams prioritize what to tackle first and determine what warrants further investigation.
If you're looking to enhance your CCTV system's privacy protection capabilities, consider exploring Secure Redact's AI-powered video redaction software. Our user-friendly platform seamlessly integrates with your existing infrastructure, ensuring efficient and reliable privacy protection.
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
Combining the manual approach with the assistance of advanced machine learning models and automation brings the best of both worlds, paired with the institutional knowledge and subject matter expertise of your team.
In the ever-evolving landscape of cybersecurity threats, organizations must continually innovate their detection methodologies to stay ahead of adversaries. Our approach leverages user behavioral analytics at three distinct levels — User Level, Peer Level and Company Level — to provide organizations with comprehensive protection and increase the accuracy of detections.
Behavioral analytics can also be applied at the Peer Level to identify cohorts of users who exhibit similar behavior patterns, regardless of their specific work functions. This approach involves clustering users based on their behavioral attributes and analyzing their collective activities. By extrapolating and analyzing user cohorts, organizations can uncover anomalies that may not be apparent at the User Level.
When selecting the best CCTV redaction software, it's important to consider features that ensure compliance with signage requirements and protect individual privacy. Look for software that allows for easy blurring or masking of identifying features, such as faces or licence plates, to maintain privacy while still leveraging the benefits of CCTV monitoring.
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
the types of scenarios where the TASER is frequently used. Page 7. 2. Page 2. Instructor Certification Course * TASER® X26 and TASER M26 Less-Lethal Weapons.
As your security camera system evolves or regulations change, it's essential to update your CCTV signage accordingly. Regularly review your signage to ensure that it accurately reflects the current monitoring setup and complies with any new legal requirements.
2021524 — Explore Fuel Oil Facts. Tevis Energy Offers High-Quality Heating Oil Throughout PA & MD. Low Heating Oil Prices. Fast Delivery. Call Now!
Ultimately, complying with CCTV signage requirements is a critical aspect of responsibly operating security cameras on your property. By understanding the legal framework, implementing clear and visible signage, and regularly reviewing your setup, you can ensure transparency, maintain trust, and minimise legal risks.
Space overview. Assembly Point is a public realm exhibition space, consisting of five glass vitrines lining the walkway between Sturt and Moore Streets, ...
Falcon Data Protection Detections uses advanced machine learning algorithms and behavioral analytics to identify anomalous patterns indicative of data exfiltration. By continuously monitoring user behavior and endpoint activities, Falcon Data Protection can detect and mitigate threats in real time, reducing the risk of data breaches and minimizing the impact on organizations' operations. Automation enables organizations to scale their response capabilities efficiently, allowing them to adapt to evolving threats and protect their sensitive assets. With automated investigation and response, security teams can shift their efforts away from sifting through vast amounts of data manually to investigating and mitigating high-priority threats.
The new Detections capability in CrowdStrike Falcon® Data Protection reduces friction for teams working to protect their organizational data, from company secrets and intellectual property to sensitive personally identifiable information (PII) or payment card industry (PCI) data. These detections are designed to revolutionize the way organizations detect and mitigate data exfiltration risks, discover unknown threats and prioritize them based on advanced machine learning models.
Videosurveillancesigns PDF
In both examples, Falcon Data Protection Detections demonstrates its ability to surface risks associated with data exfiltration and provide security teams with the insights they need to take swift and decisive action. By using advanced machine learning models and integrating seamlessly with the rest of the CrowdStrike Falcon® platform, Falcon Data Protection Detections empowers organizations to stay one step ahead of cyber threats and protect their most valuable asset — their data.
Traditional approaches to data exfiltration detection often rely on manual monitoring, which is labor-intensive and time-consuming, and strict behavior definitions, which lack important context and are inherently limited in their effectiveness. These methods struggle to keep pace with the rapidly evolving threat landscape, making it challenging for organizations to detect and mitigate data exfiltration in real time. As a result, many organizations are left vulnerable to breaches. By pairing manual data classification with the detections framework, organizations’ institutional knowledge is enhanced by the power of the Falcon platform.
When you integrate with Falcon Fusion SOAR, you can create workflows to precisely define the automated actions you want to perform in response to Falcon Data Protection Detections. For example, you can create a workflow that automatically generates a ServiceNow incident ticket or sends a Slack message when a high-severity data exfiltration attempt is detected.
In another scenario, a malicious insider may attempt to exfiltrate an unusual file type containing sensitive data by uploading it to a cloud storage service or file-sharing platform. By monitoring web upload activities and correlating them against a user’s typical file types egressed, Falcon Data Protection Detections can identify suspicious behavior indicative of unauthorized data exfiltration — even if traditional rules would have missed these events.
Stay informed, stay compliant, and prioritise privacy as you work to create a safer and more secure environment. By adhering to CCTV signage requirements and leveraging advanced technologies, you can optimise your security efforts while respecting the rights of those you serve.
CCTV signage should include clear and concise language informing individuals that they are being monitored by security cameras. The signs should be easy to read and understand, even from a distance. Common elements of CCTV signage include:
Jan 27, 2023 — Axon stock was among the market leaders and nearing a new buy point. Then things got really interesting as it unveiled the new Taser 10.
Large VideoSurveillanceSigns
The threat of data exfiltration looms over organizations of all sizes. With the introduction of Falcon Data Protection Detections, organizations now have a powerful tool to effectively identify and mitigate data exfiltration risks. Below, we delve into examples of how Falcon Data Protection Detections can identify data exfiltration via USB drives and web uploads, highlighting the ability to surface threats and prioritize them for mitigation.
For example, a disgruntled employee may connect a USB drive to transfer large volumes of sensitive data. Falcon Data Protection’s ML-based detections will identify when the number of files or file types moved deviates from that of a user’s or peer group’s typical behavior and will raise an alert, enabling security teams to investigate and mitigate the threat.
Turn the controllers on by briefly pressing the System button. · Launch the SteamVR app. · Click > Devices. · Click Pair Controller. Follow the instructions to ...
Titan Lite deliver steel carport posts and steel posts for carport columns, awning posts and corner posts to suit Goldstar Garage. Steel posts and related ...
Listen to Watch Your Step on Spotify. Song · Disclosure, Kelis · 2020.
Many states have enacted their own laws and guidelines regarding CCTV signage. For example, in California, businesses must post clear and conspicuous signs informing individuals that the premises are under video surveillance. Similarly, New York requires property owners to display signs indicating the presence of security cameras. It's crucial to research and comply with the specific regulations in your state to avoid potential legal consequences.
All-welded, 18-gauge, powder-coated steel cabinet provides extra-rigid support for cans and pails• Double-wall thermal barrier isolates flammable contents ...
Some states have more detailed requirements for CCTV signage. In Texas, for instance, signs must include the name and contact information of the entity responsible for the cameras. Elsewhere in Florida, signage must be posted at all entrances to the monitored area and must include a statement that the property is under video surveillance.

You’ll also want to stay informed about changes in federal, state, and local regulations regarding CCTV signage; attend industry events, participate in online forums, and consult with legal professionals to stay up-to-date on best practices and emerging trends.
It's important to note that federal regulations may vary depending on the specific context and use of CCTV systems. For example, the Health Insurance Portability and Accountability Act (HIPAA) sets forth strict guidelines for the use of security cameras in healthcare facilities to protect patient privacy.
Mar 28, 2024 — The OIPRD Becomes Law Enforcement Complaints Agency (LECA) ... TORONTO – On April 01, 2024, the Office of the Independent Police Review Director ( ...
Signage also helps businesses demonstrate their commitment to security and the protection of their customers, employees, and assets. By prominently displaying CCTV signs, organisations show that they take safety seriously and are actively working to create a secure environment.




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500