Kohärentes Licht – Grundlagen und Bedeutung - was ist monochromatisches licht
Here you'll find explanations and definitions of key technical terms from the fields of optics, scanner technology, laser technology and laser processing.
Bayer, U., Moser, A., Kruegel, C., Kirda, E.: Dynamic analysis of malicious code. J. Comput. Virol. 2, 67–77 (2006). https://doi.org/10.1007/s11416-006-0012-2
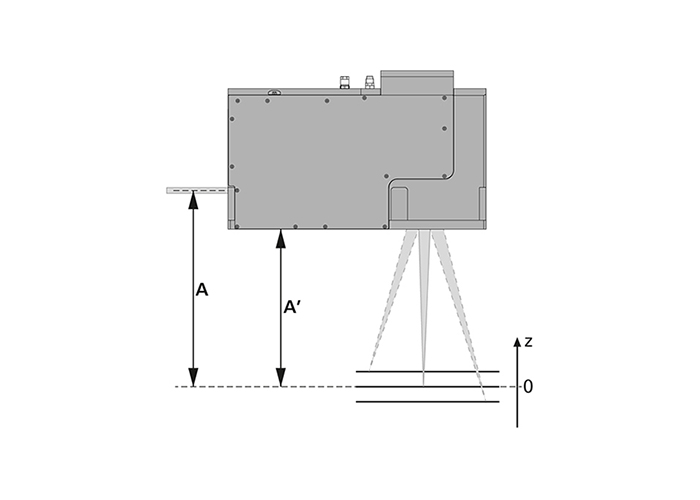
Free working distance A' is the mechanical distance between the scan system (bottom edge of housing including objective) and the "z=0" working plane.
Working distance A is the distance between the entrance aperture's central axis and the working plane. A is determined by the focal length and mounting position of the F-Theta objective (if present). For prefocus systems, working distance A is determined by the dynamic focusing unit in the null position ("z=0" plane).
2024516 — Il semplice test della vista consiste nella lettura di una tabella detta ottotipo, su cui sono impressi caratteri di grandezza crescente o ...
Nissim, N., Cohen, A., Elovici, Y.: ALDOCX: detection of unknown malicious microsoft office documents using designated active learning methods based on new structural feature extraction methodology. IEEE Trans. Inf. Forensics Secur. 12(3), 631–646 (2017)
Rieck, K., Trinius, P., Willems, C., Holz, T.: Automatic analysis of malware behavior using machine learning. J. Comput. Secur. 19(4), 639–668 (2011)
AI Art Generation Handbook/Lighting Techniques ; Photograph of Javan rhinoceros wearing a business suit screaming aloud with hands on the cheek while seeing the ...
Perdisci, R., Lanzi, A., Lee, W.: McBoost: boosting scalability in malware collection and analysis using statical classification of executables. In: Computer Security Applications Conference (2008). https://doi.org/10.1109/ACSAC.2006.53
Boldewin, F.: Analyzing MSOffice malware with OfficeMalScanner. https://ja.scribd.com/document/21143233/Analyzing-MSOffice-Malware-With-OfficeMalScanner
Naser, A., Hadi, A.: Analyzing and detecting malicious content: DOCX files. Int. J. Comput. Sci. Inf. Secur. (IJCSIS) 14(8), 404–412 (2016)
Mimura, M., Otsubo, Y., Tanaka, H.: Evaluation of a brute forcing tool that extracts the RAT from a malicious document file. In: 2016 11th Asia Joint Conference on Information Security (Asia JCIS) (2016). https://doi.org/10.1109/AsiaJCIS.2016.10
Explore books by Paolo Crepet with our selection at Waterstones.com. Click and Collect from your local Waterstones or get FREE UK delivery on orders over ...
Beugung und Interferenz erfordern kohärente Wellen. Zwei Wellen sind kohärent zueinander, wenn sie eine feste Phasenbeziehung besitzen. Dies ist der Fall ...
Liu, D., Wang, H., Stavrou, A.: Detecting malicious Javascript in PDF through document instrumentation. In: 2014 44th Annual IEEE/IFIP International Conference Dependable Systems and Networks (DSN), pp. 100–111, ISBN 978-1-4799-2233-8 (2014)
In recent years, the number of targeted email attacks which use Microsoft (MS) document files has been increasing. In particular, damage by malicious macros has spread in many organizations. Relevant work has proposed a method of malicious MS document files detection. To the best of our knowledge, however, no method of detecting malicious macros exists. Hence, we proposed a method which detects malicious macros themselves using machine learning. First, the proposed method creates corpuses from macros. Our method removes trivial words in the corpus. It becomes easy for the corpuses to classify malicious macros exactly. Second, Doc2Vec represents feature vectors from the corpuses. Malicious macros contain the context. Therefore, the feature vectors of Doc2Vec are classified with high accuracy. Machine learning models (Support Vector Machine, Random Forest and Multi Layer Perceptron) are trained, inputting the feature vectors and the labels. Finally, the trained models predict test feature vectors as malicious macros or benign macros. Evaluations show that the proposed method can obtain a high F-measure (0.93).
Miura, H., Mimura, M., Tanaka, H. (2018). Macros Finder: Do You Remember LOVELETTER?. In: Su, C., Kikuchi, H. (eds) Information Security Practice and Experience. ISPEC 2018. Lecture Notes in Computer Science(), vol 11125. Springer, Cham. https://doi.org/10.1007/978-3-319-99807-7_1
By transforming lasers into universal tools, scanning solutions help to add functionality and value to materials. SCANLAB's broad palette of scanning solutions fulfills demands for higher speed, more precision, greater efficiency or improved environmental compatibility.
100mm O.D.; Adjustable iris; Provides darkfield observation especially for gemology and jewelry making.
L'obiettivo CN8x15 IAS S E1/P1 Cine Servo montato su una fotocamera Canon. Grazie alla sua lunghezza focale da grandangolo a teleobiettivo, CN8x15 IAS S E1/P1 è ...
Wolf in sheep’s clothing: a SophosLabs investigation into delivering malware via VBA. https://nakedsecurity.sophos.com/2017/05/31/wolf-in-sheeps-clothing-a-sophoslabs-investigation-into-delivering-malware-via-vba/
This is a 4-pin circular connector cable with a right angle connector on one end and a straight 4-pin circular connector on the other end.
Otsubo, Y., Mimura, M., Tanaka, H.: O-checker: detection of malicious documents through deviation from file format specification. In: Black Hat USA (2016)
Quindi, per esempio, data una lunghezza focale del tuo obiettivo di X e una apertura diaframma di Y, se la distanza iperfocale è 5 metri significa che sarà ...
Corona, I., Maiorca, D., Giacinto, G.: Lux0R: detection of malicious PDF-embedded JavaScript code through discriminant analysis of API references (2014)
Cyth Systems was founded in 1999 and is a leading integration and engineering firm with a proven track record of success designing and building automated ...
Specifically made to be the best intro microscope available, comes with 40-1000x magnifications, and it's upgradeable; you can buy it with ...




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500