Gloves Required Signs - gloves sign
Behavioral analytics can also be applied at the Peer Level to identify cohorts of users who exhibit similar behavior patterns, regardless of their specific work functions. This approach involves clustering users based on their behavioral attributes and analyzing their collective activities. By extrapolating and analyzing user cohorts, organizations can uncover anomalies that may not be apparent at the User Level.
TASERmodels
After it’s signed it’s up to you on how to export your taser xp26 test: download it to your mobile device, upload it to the cloud or send it to another party via email. The airSlate SignNow application is equally effective and powerful as the web solution is. Get connected to a reliable web connection and start completing documents with a legally-binding signature within a few minutes.
After that, your taser xp26 test is ready. All you have to do is download it or send it via email. airSlate SignNow makes signing easier and more convenient since it offers users a number of additional features like Merge Documents, Add Fields, Invite to Sign, etc. And due to its multi-platform nature, airSlate SignNow can be used on any gadget, PC or mobile, regardless of the OS.
Bid farewell to lost or misplaced documents, tedious form searches, or errors that necessitate printing new copies. airSlate SignNow fulfills all your document management requirements in just a few clicks from any device you prefer. Edit and eSign taser written test x26p and ensure outstanding communication at every stage of your form preparation with airSlate SignNow.
TASER10
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
TASERX26C
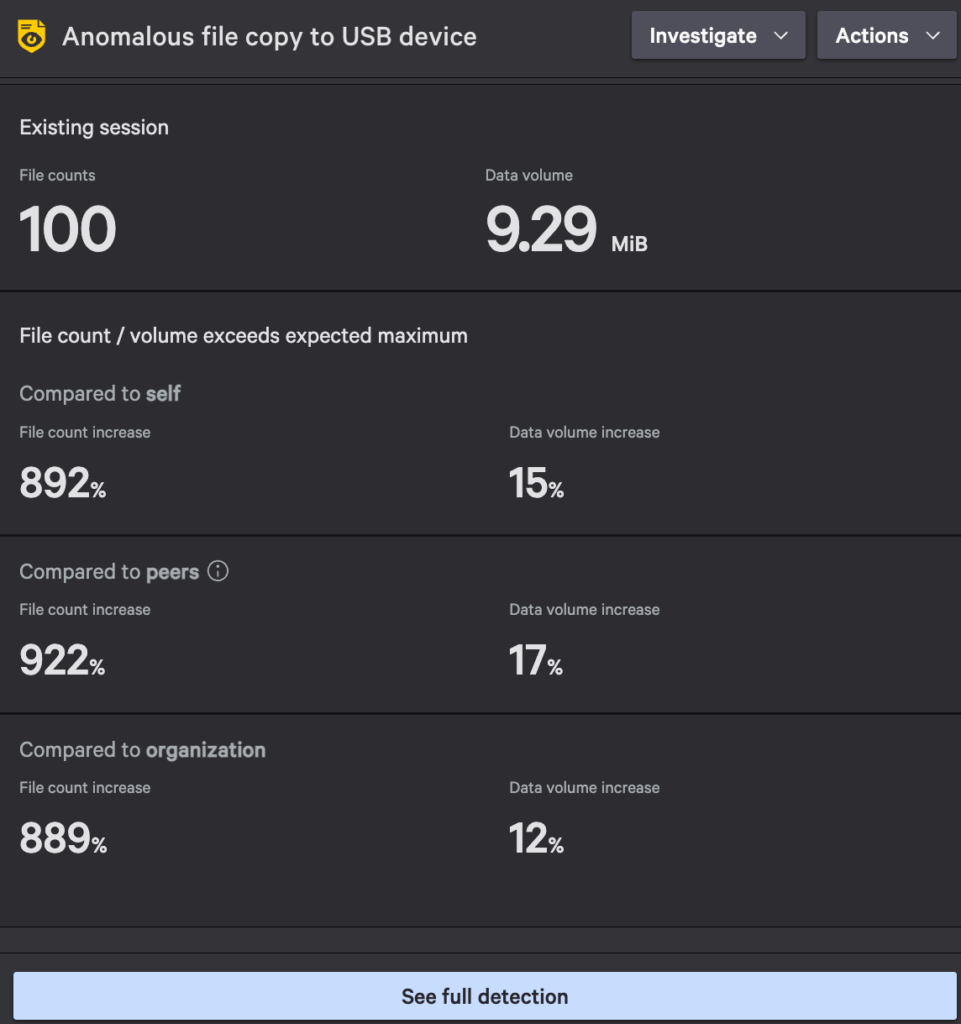
For example, a disgruntled employee may connect a USB drive to transfer large volumes of sensitive data. Falcon Data Protection’s ML-based detections will identify when the number of files or file types moved deviates from that of a user’s or peer group’s typical behavior and will raise an alert, enabling security teams to investigate and mitigate the threat.
In both examples, Falcon Data Protection Detections demonstrates its ability to surface risks associated with data exfiltration and provide security teams with the insights they need to take swift and decisive action. By using advanced machine learning models and integrating seamlessly with the rest of the CrowdStrike Falcon® platform, Falcon Data Protection Detections empowers organizations to stay one step ahead of cyber threats and protect their most valuable asset — their data.
Falcon Data Protection Detections uses advanced machine learning algorithms and behavioral analytics to identify anomalous patterns indicative of data exfiltration. By continuously monitoring user behavior and endpoint activities, Falcon Data Protection can detect and mitigate threats in real time, reducing the risk of data breaches and minimizing the impact on organizations' operations. Automation enables organizations to scale their response capabilities efficiently, allowing them to adapt to evolving threats and protect their sensitive assets. With automated investigation and response, security teams can shift their efforts away from sifting through vast amounts of data manually to investigating and mitigating high-priority threats.
If you want to share the taser xp26 test with other people, you can send the file by electronic mail. With airSlate SignNow, you cane Sign as many papers in a day as you require at an affordable price. Start automating your signature workflows right now.
At the Company Level, user behavioral analytics are magnified to account for the nuances of each organization's business processes and to tailor anomalies to their expected activity. This involves incorporating domain-specific knowledge and contextual understanding of the organization's workflows and operations based on file movements and general data movement.
If you own an iOS device like an iPhone or iPad, easily create electronic signatures for signing a taser xp26 in PDF format. airSlate SignNow has paid close attention to iOS users and developed an application just for them. To find it, go to the App Store and type airSlate SignNow in the search field.
Google Chrome’s browser has gained its worldwide popularity due to its number of useful features, extensions and integrations. For instance, browser extensions make it possible to keep all the tools you need a click away. With the collaboration between airSlate SignNow and Chrome, easily find its extension in the Web Store and use it to design taser xp26 right in your browser.
An eDocument can be considered legally binding given that particular requirements are satisfied. They are especially vital when it comes to signatures and stipulations related to them. Entering your initials or full name alone will not ensure that the organization requesting the form or a court would consider it executed. You need a trustworthy solution, like airSlate SignNow that provides a signer with a digital certificate. Furthermore, airSlate SignNow maintains compliance with ESIGN, UETA, and eIDAS - major legal frameworks for eSignatures.
Detect, prevent, and respond to attacks— even malware-free intrusions—at any stage, with next-generation endpoint protection.
TASERX2
Speed up your business’s document workflow by creating the professional online forms and legally-binding electronic signatures.
Despite iPhones being very popular among mobile users, the market share of Android gadgets is much bigger. Therefore, airSlate SignNow offers a separate application for mobiles working on Android. Easily find the app in the Play Market and install it for signing your taser xp26.
As the society ditches in-office working conditions, the completion of documents more and more takes place electronically. The taser x2 user certification test isn’t an any different. Handling it utilizing digital tools differs from doing this in the physical world.
When you integrate with Falcon Fusion SOAR, you can create workflows to precisely define the automated actions you want to perform in response to Falcon Data Protection Detections. For example, you can create a workflow that automatically generates a ServiceNow incident ticket or sends a Slack message when a high-severity data exfiltration attempt is detected.
By aligning detection algorithms with the organization's unique business processes, security teams can more accurately identify deviations from expected activity and prioritize them based on their relevance to the organization's security posture. For example, anomalies that deviate from standard workflows or access patterns can be flagged for further investigation, while routine activities are filtered out to minimize noise. Additionally, behavioral analytics at the Company Level enable organizations to adapt to changes in their environment such as organizational restructuring, new business initiatives or shifts in employee behavior. This agility ensures detection capabilities remain relevant and effective over time.
TASERX26 price
Mobile devices like smartphones and tablets are in fact a ready business alternative to desktop and laptop computers. You can take them everywhere and even use them while on the go as long as you have a stable connection to the internet. Therefore, the airSlate SignNow web application is a must-have for completing and signing taser xp26 on the go. In a matter of seconds, receive an electronic document with a legally-binding signature.
Compliance with eSignature regulations is only a fraction of what airSlate SignNow can offer to make form execution legitimate and secure. Furthermore, it offers a lot of opportunities for smooth completion security smart. Let's quickly run through them so that you can be assured that your taser certificate remains protected as you fill it out.
The airSlate SignNow extension was developed to help busy people like you to decrease the stress of signing legal forms. Begin signing taser xp26 test using our tool and become one of the numerous satisfied clients who’ve already experienced the advantages of in-mail signing.
For example, if an employee and their peers typically only handle office documents, but one day the employee begins to upload source code files to the web, a detection will be created even if the volume of activity is low, because it is so atypical for this peer group. This approach surfaces high-impact events that might otherwise be missed by manual triage or rules based on static attributes.
TASERx27
Digital document management has gained traction among businesses and individuals alike. It offers an excellent environmentally friendly alternative to conventional printed and signed papers, allowing you to obtain the right format and securely archive it online. airSlate SignNow equips you with all the necessary tools to create, edit, and eSign your documents swiftly and efficiently. Manage taser exam on any device using airSlate SignNow's Android or iOS applications and streamline any document-driven process today.
Are you looking for a one-size-fits-all solution to design taser xp26? airSlate SignNow combines ease of use, affordability and security in one online tool, all without forcing extra DDD on you. All you need is smooth internet connection and a device to work on.
Combining the manual approach with the assistance of advanced machine learning models and automation brings the best of both worlds, paired with the institutional knowledge and subject matter expertise of your team.
The threat of data exfiltration looms over organizations of all sizes. With the introduction of Falcon Data Protection Detections, organizations now have a powerful tool to effectively identify and mitigate data exfiltration risks. Below, we delve into examples of how Falcon Data Protection Detections can identify data exfiltration via USB drives and web uploads, highlighting the ability to surface threats and prioritize them for mitigation.
The new Detections capability in CrowdStrike Falcon® Data Protection reduces friction for teams working to protect their organizational data, from company secrets and intellectual property to sensitive personally identifiable information (PII) or payment card industry (PCI) data. These detections are designed to revolutionize the way organizations detect and mitigate data exfiltration risks, discover unknown threats and prioritize them based on advanced machine learning models.
X26TaserAmazon
Once you’ve finished signing your taser xp26 test, choose what you should do after that — save it or share the doc with other parties involved. The airSlate SignNow extension gives you a selection of features (merging PDFs, including several signers, etc.) for a much better signing experience.
At the User Level, behavioral analytics are employed to understand and contextualize each individual user's benchmark activity against their own personal history. By analyzing factors such as file activity, access patterns and destination usage, organizations can establish a baseline of normal behavior for each user.
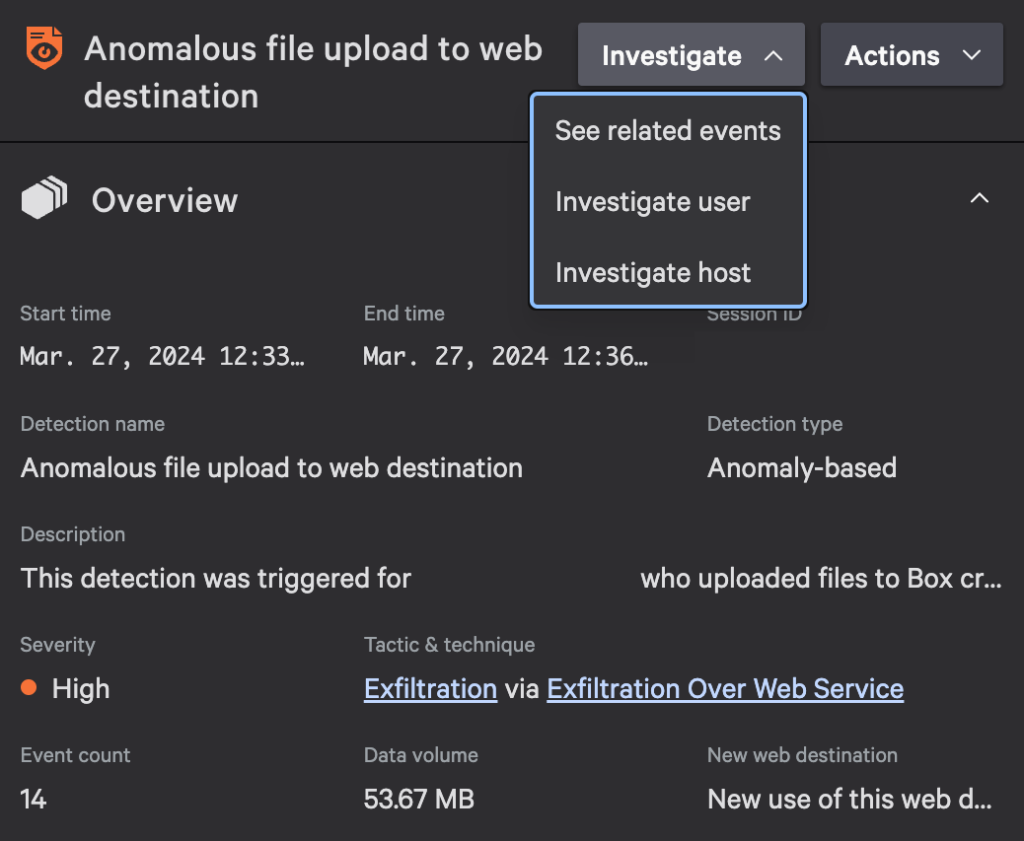
The Details panel includes the detection’s number of files and data volume moved versus the established baselines per user, peers and the organization. This panel also contains contextual factors such as first-time use of a USB device or web destination, and metadata associated with the file activity, to better understand the legitimate reasons behind certain user behaviors. This nuanced approach provides a greater level of confidence that a detection indicates a true positive for data exfiltration.
Using machine learning algorithms, anomalies that deviate from this baseline are flagged as potential indicators of data exfiltration attempts.
In another scenario, a malicious insider may attempt to exfiltrate an unusual file type containing sensitive data by uploading it to a cloud storage service or file-sharing platform. By monitoring web upload activities and correlating them against a user’s typical file types egressed, Falcon Data Protection Detections can identify suspicious behavior indicative of unauthorized data exfiltration — even if traditional rules would have missed these events.
TASERX26P Discontinued
Filling out the taser certificate fillable with airSlate SignNow will give better confidence that the output template will be legally binding and safeguarded.
Due to the fact that many businesses have already gone paperless, the majority of are sent through email. That goes for agreements and contracts, tax forms and almost any other document that requires a signature. The question arises ‘How can I design the taser xp26 I received right from my Gmail without any third-party platforms? ’ The answer is simple — use the airSlate SignNow Chrome extension.
Traditional approaches to data exfiltration detection often rely on manual monitoring, which is labor-intensive and time-consuming, and strict behavior definitions, which lack important context and are inherently limited in their effectiveness. These methods struggle to keep pace with the rapidly evolving threat landscape, making it challenging for organizations to detect and mitigate data exfiltration in real time. As a result, many organizations are left vulnerable to breaches. By pairing manual data classification with the detections framework, organizations’ institutional knowledge is enhanced by the power of the Falcon platform.
The whole procedure can last a few seconds. As a result, you can download the signed taser xp26 test to your device or share it with other parties involved with a link or by email. Because of its multi-platform nature, airSlate SignNow is compatible with any gadget and any OS. Use our signature tool and leave behind the old days with efficiency, security and affordability.
Time is of the essence when it comes to protecting your data, and often, teams are sifting through hundreds or thousands of alerts to try to pinpoint truly malicious user behavior. Manual triage and response takes up valuable resources, so machine learning can help busy teams prioritize what to tackle first and determine what warrants further investigation.
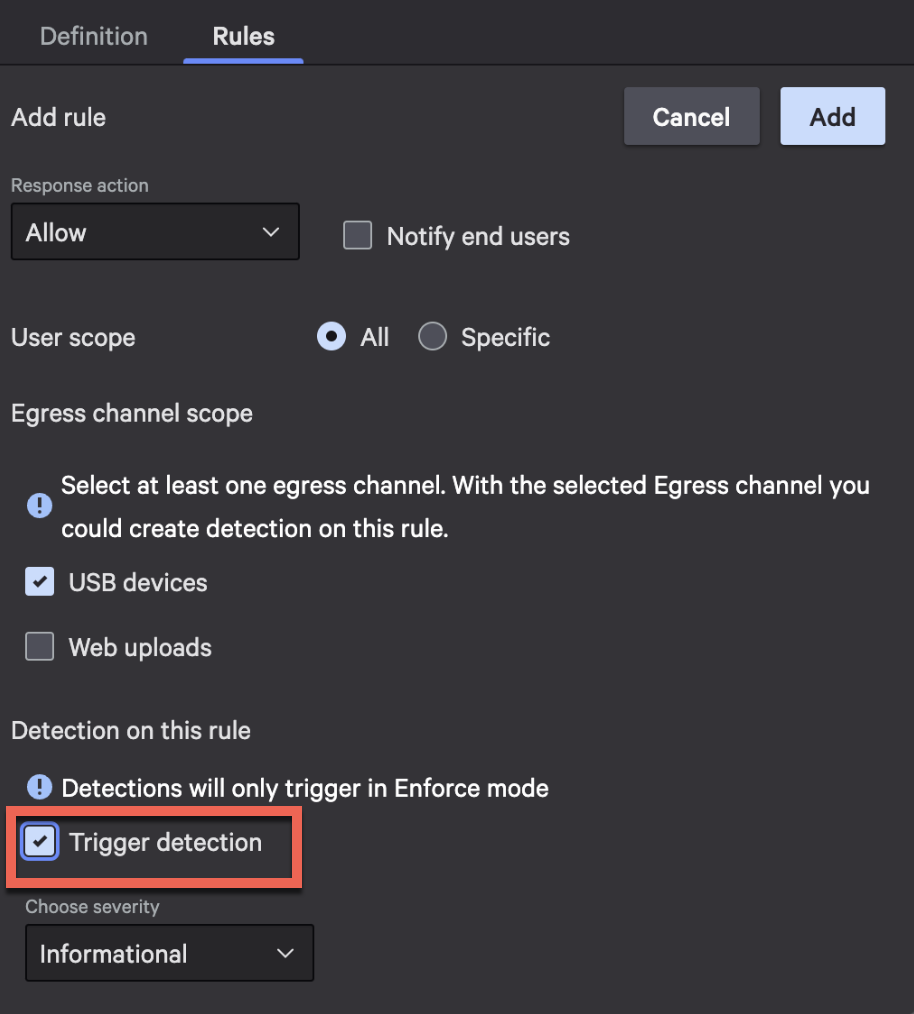
In addition to the aforementioned anomaly detections, you can configure rule-based detections associated with your data classifications. This enhances the power of data classification to assign severity, manage triage and investigation, and trigger automated workflows. Pairing these with anomaly detections gives your team more clarity into what to pursue first and lets you establish blocking policies for actions that should not occur.
Forget about scanning and printing out forms. Use our detailed instructions to fill out and eSign your documents online.
In the ever-evolving landscape of cybersecurity threats, organizations must continually innovate their detection methodologies to stay ahead of adversaries. Our approach leverages user behavioral analytics at three distinct levels — User Level, Peer Level and Company Level — to provide organizations with comprehensive protection and increase the accuracy of detections.




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500