Emergency eyewash and safety shower station - emergency shower and eyewash
Drones were later used in the gulf war and became more capable over time of offering real time surveillance and carrying weapons. Today, the United States army has 7,494 drones accounting for 1 out of every 3 U.S army aircraft. Army pilots now sit in rooms just outside Las Vegas, flying drones that are halfway around the world in Afghanistan and Iraq, carrying out surveillance and launching attacks.
Beechcraft later designed the MQM-61 cardinal in 1955, shown above, a drone that built on the Radioplane OQ 2 and was designed for soldiers to practice air to air combat training. It carried targets and soldiers had to shoot the targets while flying in their own aircraft. Only 2,200 of these drones were ever built.
The ids_rules_file variable specifies a defined location for the local.rules file, while the ids_rule_state variable indicates that the rule should be created if it does not already exist.
Whoinvented dronesWikipedia
You can use Ansible to automate your Intrusion Detection and Prevention System (IDPS). For the purpose of this guide, we use Snort as the IDPS. Use Ansible automation hub to consume content collections, such as tasks, roles, and modules to create automated workflows.
World War II ushered in a new era of drone development. Denny Reginald, a famous actor and model aircraft enthusiast bought a model plane design from Walter Righter. He saw potential for the model aircraft to be used for soldiers to target practice with. The drone was launched by catapult and if it was not shot down during the target practice it would land by parachute at the end. The OQ 2 as he called it, shown above, took flight in 1939 and became the first mass produced drone in the United States with 15,000 eventually built. Marilyn Monroe began her career working at Radioplane, the company who manufactured the OQ 2 drone. She worked in the assembly line and later after being spotted by army photographer David Conover was persuaded to instead switch career paths and become a model. Northprop Grumman eventually bought out the Radioplane company in 1952.
Once you run the playbook, all of your tasks will be executed in addition to your newly created rules. Your playbook output will confirm your PLAY, TASK, RUNNING HANDLER, and PLAY RECAP.
Add the following tasks and task-specific variables (e.g., rules, Snort rules file, and the state of the rule - present or absent) to the playbook:
Whenwas drone camerainvented
Drones have only begun becoming known to much of the general public, however many people are unaware of the much more extensive history of drones. Drones in fact have been around over 100 years despite only seeing their commercial development take off in recent years.
History ofdrones
Use the ids_rule role to manage your rules and signatures for IDPS. For example, you can set a new rule that looks for a certain pattern aligning with a previous attack on your firewall.
To verify that your IDPS rules were successfully created, SSH to the Snort server and view the content of the /etc/snort/rules/local.rules file.
History ofdronestimeline
When were dronesfirst used in war
Toward the end of the 1950’s the U.S Army began stepping up drone development to avoid losing pilots over hostile territory. This led to the Lockheed D-21. The Lockheed D-21 went beyond the traditional use of drones for target practice and was designed to carry a camera module over enemy territory and gather intelligence. In the 1970’s Israel developed the first drones with real time surveillance leading to the neutralization of Syrian air defenses at the start of the 1982 Lebanon War.
Tasks are components that make changes on the target machine. Since you are using a role that defines these tasks, the include_role is the only entry you need.
On Aug. 22, 1849, after months of trial and error Austria launched a pilot-less balloon bomb attack against Venice. The balloon did not cause much damage but it led the way for the use of drones. Later in 1915, Nikola Tesla described a fleet of unmanned aerial combat vehicles.
Drone use goes far beyond just the military, and in 1987, Yamaha came out with a crop spraying drone. The drone did not take off in many places outside Japan, and after almost 30 years it finally received permission to fly in the United States in 2015. Consumer drones took off with the Parrot drone in 2010 followed by the popular DJI Phantom in 2013. These drones were the first to become affordable to the general public and were mainly designed to capture aerial photography with. Smartphones are credited with bringing down the price and size of many components for consumer drones allowing them to finally take off. GPS, processors, cameras, and gyroscopes are some of the equipment that became suitable for use on drones after their use in smartphones drove development of smaller and cheaper versions. Today, consumers can buy drones for as little as $25 and their capabilities are only beginning to be realized in this space.
To automate your IDPS, use the ids_rule role to create and change Snort rules. Snort uses rule-based language that analyzes your network traffic and compares it against the given rule set.
When were drones inventedand by whom
Red Hat is committed to replacing problematic language in our code, documentation, and web properties. For more details, see the Red Hat Blog.
First drone camera in the world
We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.
Once you confirm the service is actively running, exit the Snort server by simultaneously pressing CTRL and D, or by typing exit on the command line. All further interaction will be done through Ansible from the Ansible control host.

When weremoderndrones invented
Before you begin automating your IDPS with Ansible, ensure that you have the proper installations and configurations necessary to successfully manage your IDPS.
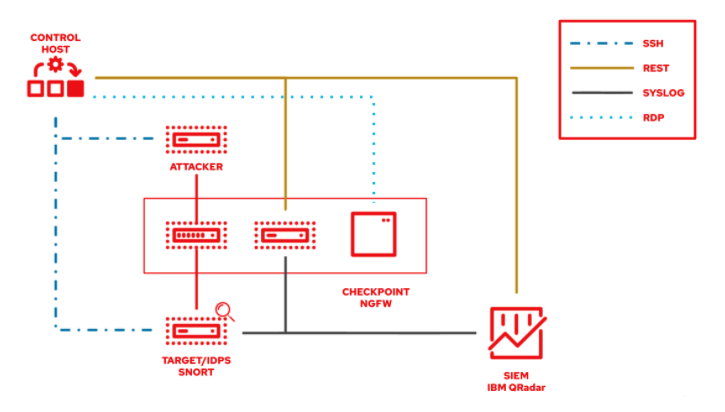
The following lab environment demonstrates what an Ansible security automation integration would look like. A machine called “Attacker” simulates a potential attack pattern on the target machine on which the IDPS is running.




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500