Real time crime centers, which started in bigger cities ... - real-time crime centers
Ninety dollars
The next day following a call for service, the reporting person will receive a text message with a link to complete a short survey about the police response and their interaction with members of the Newark Police Department, including the communications officers and any responding police officers. The Newark Police Department will then use that information to ensure that members of our agency are providing the best service possible.
The Newark Police Department affirms that all suspects and defendants listed on this site are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
My Ninety EOS
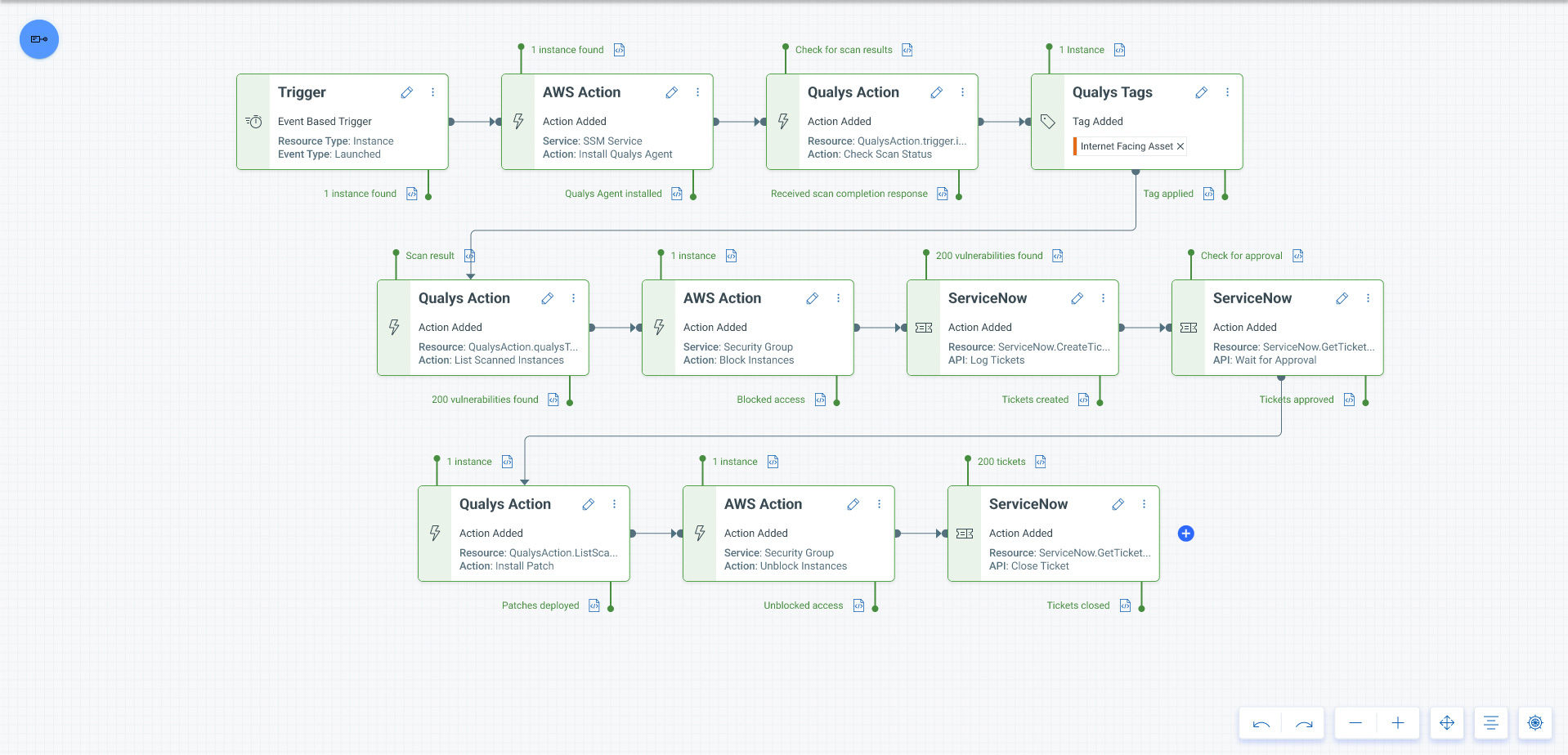
Since we only want to scan Internet-facing assets, the next step is to check whether the virtual machine has a public IP address. We will assign an “external” Qualys tag using the Tagging node. Assigning Qualys tags is recommended for assets so you can use them later in other workflows. An example is creating vulnerability reports specific to virtual machines with external tags.
Qualys makes this possible through a new offering called Qualys Flow. Qualys Flow is a no-code automated workflow creation capability that allows you to build workflows, known as QFlows. It provides end-to-end orchestration of detection and remediation processes within the Qualys Cloud Platform as well as from your cloud infrastructure such as AWS. Qualys Flow visualizes the logical flow of events, data, and actions in the form of nodes, each of which delivers a specific function in the detection, analysis, or remediation chain. QFlows can be created directly in the UI by dragging and dropping nodes and configuring them as needed.
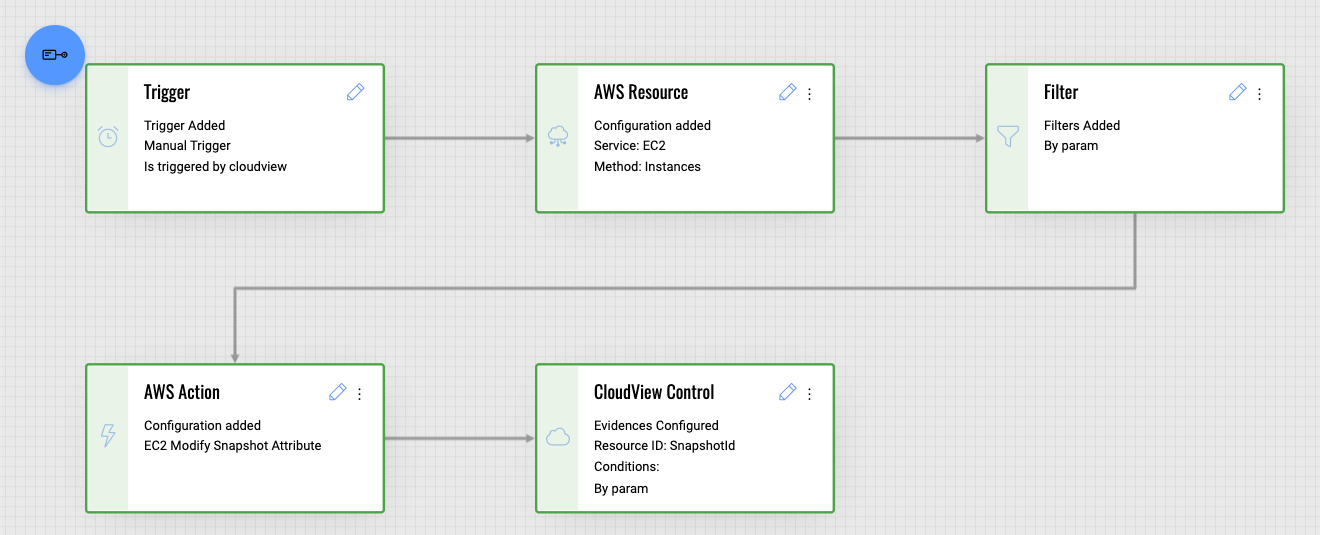
Using Qualys Flow, the Cybersecurity team can detect whether backups are encrypted and then encrypt them if they aren’t, as shown below. In this way, QFlow does its part to enforce security best practices automatically. Set it and forget it.
Upon completion of the scan, we check the virtual machine’s Qualys TruRisk score to verify that it is >900. The TruRisk score is calculated by analyzing several factors, including CVSS scores, asset criticality, etc., to establish that asset’s overall risk level. The TruRisk score ranges between 0 and 1000, with 0 representing the lowest risk and 1000 representing the highest risk. The TruRisk scoring model indicates that a virtual machine with a score >900 should be quarantined immediately.
Ninety io app download
The threat landscape is rapidly and constantly evolving. New software vulnerabilities and service misconfigurations are discovered daily, and exploits targeting them are often released within hours. For effective security, pursuing the automation of both detection and remediation processes is essential.
Qualys Flow empowers cybersecurity professionals to create powerful security automation workflows without writing a single line of code. Actions are orchestrated across Qualys cloud services, third-party applications, and cloud service providers using QFlow nodes arranged in a logical process. Many templated workflows are available out-of-the-box in QFlow. These templates can be used as-is or customized to meet your specific needs.
Our next step is to quarantine the virtual machine. We do this by attaching a deny-all security group to it, preventing all communication with the network. In Qualys Flow, you can perform any action that the cloud service provider’s API supports. This means you can perform other actions, such as suspending or terminating the virtual machine, to quarantine the virtual machine.
Ninty or ninety
Qualys Flow is now generally available and currently supports workflows for AWS and Azure cloud. Interested parties can get started with QFlow for free by signing up for a free trial of Qualys CloudView here. Existing Qualys customers can try QFlow by contacting their Technical Account Manager for set up.
All QFlows begin with a Trigger node, which specifies what event triggers the workflow. For this QFlow, we have configured the Trigger node to listen for a new virtual machine event.
Non-cloud environments are supported. Using the HTTP node, you can access any public endpoint, including Qualys API or any other service. We are building out-of-the-box integration to popular tools, but you can use any HTTP service. Let me know if you have a specific use case in mind and I can comment on the feasibility to implement it.
ninety.io login
This looks very good Parag. Support currently for AWS/Azure. When will it be available for the non-cloud environment please ?
From Kona Shen, Axon’s VP and GM of My90: “We are excited to be supporting Newark PD’s mission to serve the public with smart, modern, and compassionate policing. We know that this type of feedback can build trust, strengthen relationships, and improve safety and we admire Newark PD’s commitment to using this feedback to serve their community.”
Ninety-five
The Newark Police Department has launched Axon’s engagement platform, My90, as part of an ongoing commitment to serving the public with modern and compassionate policing. Newark PD is the first agency in Delaware to use the My90 platform.
We then notify the IT Operations and Cybersecurity teams about the quarantined VM by creating a ServiceNow ticket. Any remediation actions will require approval. As soon as the approval has been received, Qualys patches the VM automatically, removes it from quarantine by detaching it from the security group, and then closes the ServiceNow ticket.
After assigning the tag, we now conduct a perimeter scan using a Qualys Action node. Qualys Action nodes allow you to call Qualys APIs for the supported application(s).
You are invited to join Qualys at AWS re:Inforce, being held July 26-27th in Boston. Drop by Booth #111 to learn about Qualys Flow. Visit this site to learn more.
IT organizations frequently take snapshots of their virtual machines for backup purposes. One of the frequent mistakes we have seen customers make is forgetting to encrypt backups. If your organization suffers a breach, hackers can easily access the data in your virtual machines if your backups are not encrypted.
Qualys Flow also integrates with Qualys CloudView. You can create a custom control in CloudView by simply linking it to a QFlow.
Ninite
From Police Chief Mark Farrall: “We have a long history of interacting with the community and making internal policy changes based upon feedback from the community. This program will allow us to get that information quickly from those who have had contact with our personnel.”
The Newark Police Department has been conducting community surveys for many years. While the surveys were originally conducted via US Mail, the agency has more recently transitioned to a web-based survey. Any member of the public, including victims, witnesses and defendants, may continue to use the web-based survey to provide feedback to the Newark Police Department. The web-based survey can be found here.
Ninety software
The Newark Police Department affirms that all suspects and defendants listed on this site are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
Here’s an example from Qualys Flow for orchestrating and automating a workflow for risk assessment, vulnerability assessment, and remediation of a newly deployed virtual machine.
Several factors make security automation particularly challenging. First, the complexity of handoffs between Cybersecurity and IT Operations teams. Second, the need to orchestrate multiple tools such as security, change management, and alerting. A typical cybersecurity process in an enterprise looks like the following:
My90 is a tool used to engage the public, collect feedback, and improve outcomes following service calls. Community members use My90 to provide valuable input while maintaining their privacy. Agencies use My90 to better understand the impact they are having within their communities, from what is working well to what needs extra attention.
On average, most enterprises take 45 days to patch a high-criticality vulnerability, according to Qualys research. The main reason is cascading delays due to poor orchestration of the various steps outlined above.




 Ms.Cici
Ms.Cici 
 8618319014500
8618319014500